By: Nawa Single
Eva Chen started the conference with a history of the paper media found Cai Lun (50-121 AD). A number of knowledge scattered with papers. Now, the information spreads through the internet. Reasonable to give birth to new business: information security and data protection on the internet.
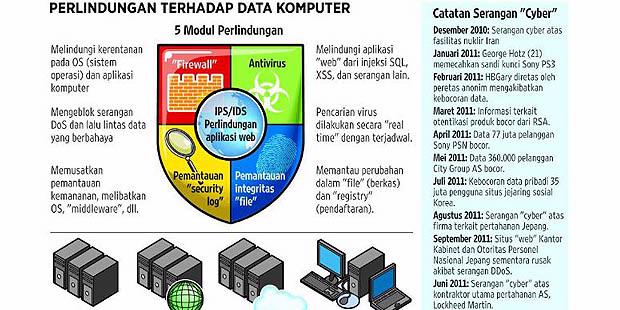
December 2010, attacks via the Internet are directed to the manager of Iran's nuclear facilities. Activities that could potentially compromise the security of attacks globally, "said Eva Chen, Top Executive Officers (Chief Executive Officer / CEO) Trend Micro, in a media conference in Taiwan mid-April 2012.
Chen co-founded the company Trend Micro 1988 in New York, United States. The company offers the services of digital information security solutions and are now based in Tokyo, Japan.
Digital information security solutions include protection of physical, virtual, and cloud computing systems. There are five modules developed protection Trend Micro, which is a web application protection, firewall, antivirus, security log monitoring, and monitoring an integrated file.
Protection to be done in layers of cloud computing. At first, such as the identification of assault with a monitoring camera. If the attack continues, there is a warning system. If the attack continues, launched counter-action.
Chen is not willing to do detailing the company's protection program. This is so as not to reveal the weak points of protection.
Vandal and thief
Initially, in 1982, computer users are very careful in using the diskette. When it is pointed out as a floppy disk spreaders of computer viruses which could damage, disrupt, or eliminating programs and data.
Now the virus is only spread via floppy disks or computer hardware, but via the Internet. It lasted from the year 1987-1988. Now developed into a vandal and theft of data for various purposes. The attack, which eliminates the program and can cause loss of data is priceless.
Internet-based computing technology is evolving rapidly. In 2007-2008 began to hear the term cloud computing (cloud computing). Cloud computing paradigm of information stored permanently on server (provider) who can be hired, that would be used only data that is stored temporarily in the user's computer.
Computers were increasingly developed mini. However, the capacity to present information from the Internet to nearly infinite.
Cloud computing has a complex infrastructure. Users can access to gain information needed. However, most users do not know what's inside. Also do not know who the expert is to package information.
Users also do not have control over their cloud computing infrastructure. These things as a weakness when the associated issues of data security.
Chen said, cyber attacks (attacks via the Internet) continues to be a threat. After the attack on Iranian nuclear facilities, carrying a variety of attacks that result in data leakage or data of individual institutions.
On April 2011, 77 million consumers Sony PSN stolen data. Then in May 2011, 360 000 consumers in the U.S. theft of data. June 2011, turn 35 million users of social networking sites Korea stolen data.
Optimize the business
Cloud computing is very useful to optimize the sales of a product. As for individual users easily achieve the benefits of cloud computing. Wherever there is a network throughout the Internet, users can open the electronic mail.
Cloud computing provides benefits, but also involve risks. Therefore, data security becomes important. Security is offered by Trend Micro.
In a series of media conferences in Taiwan, exemplified by the use of cloud computing to optimize the industrial enterprises in telecommunications, namely Chungwa Telecom, Taiwan. Fu-Kuei Chung, Data Communication Business Group Chungwa Telecom, said the data security of cloud computing utilization of 76 percent.
"To ensure and improve data security, Chungwa Telecom in collaboration with Trend Micro," said Chung.
He said the collaboration with Trend Micro Chungwa Telecom took place since the years 2004-2005, using a virus scan and antivirus products. In 2012, developed antihacking collaboration with Trend Micro. A year earlier, 2011, it put the data on cloud computing and Amazon S3 CloudBox.
Chen said, now hackers are also targeting mobile device users of cloud computing (mobile).
Security protection beyond the use of cloud computing becomes absolutely necessary. In Indonesia, the use of cloud computing in the public interest still needs to be optimized.
-
 9:24 AM
9:24 AM

0 komentar:
Post a Comment